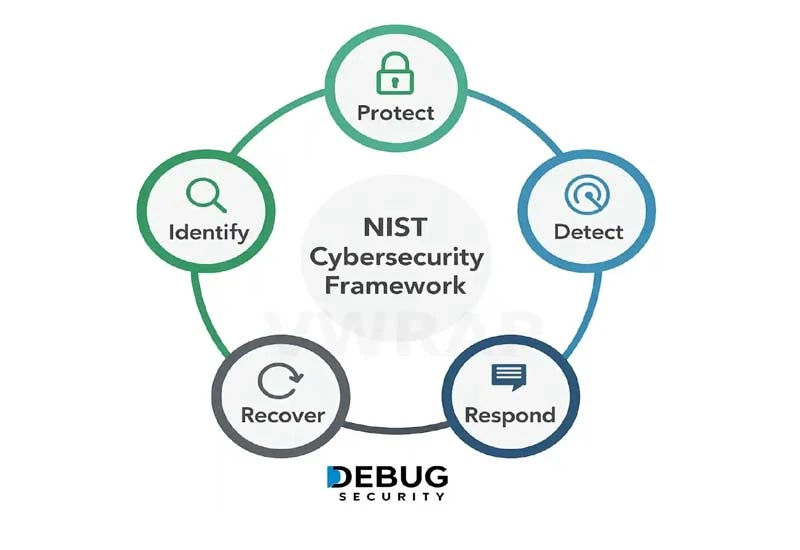
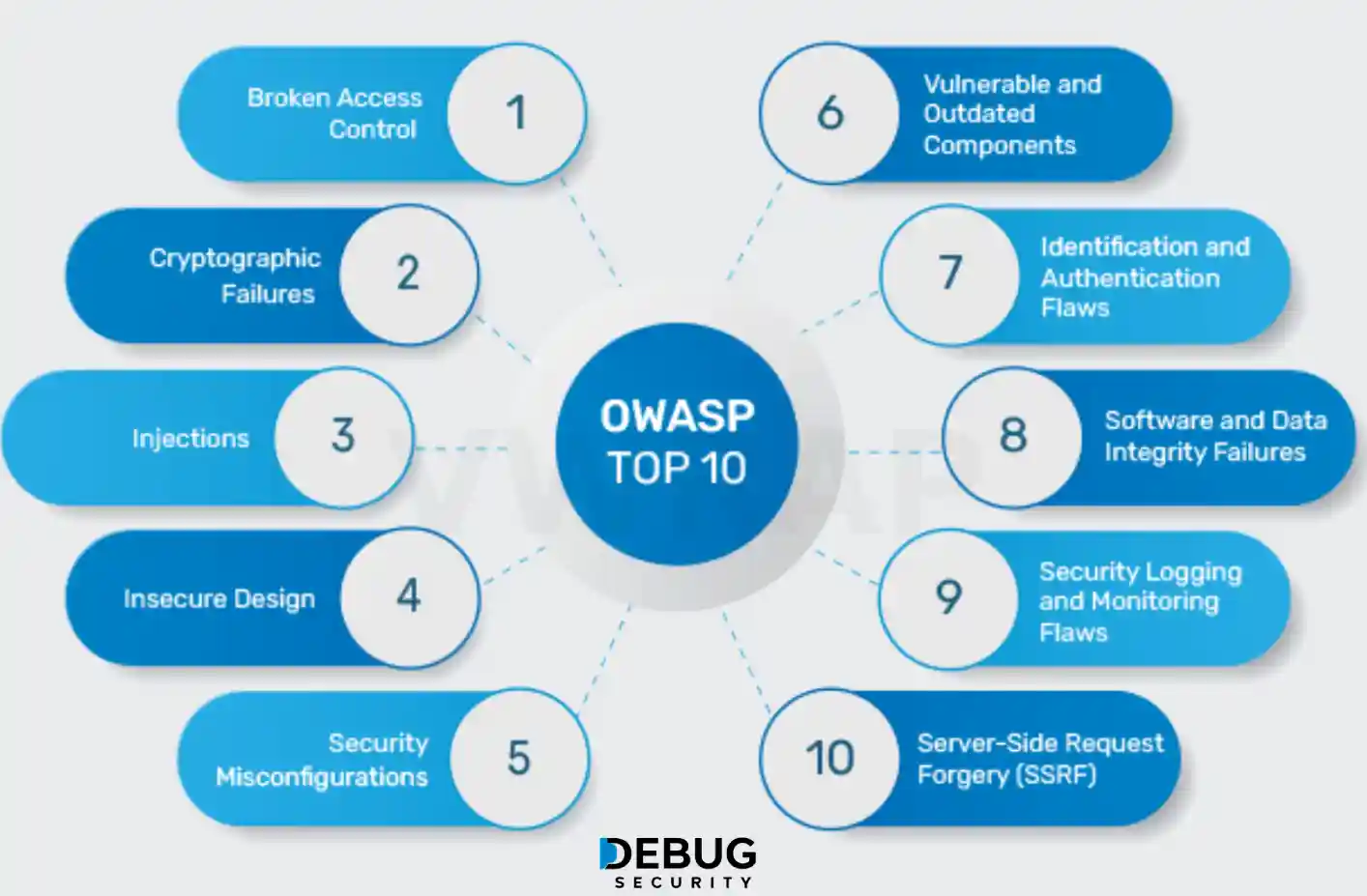
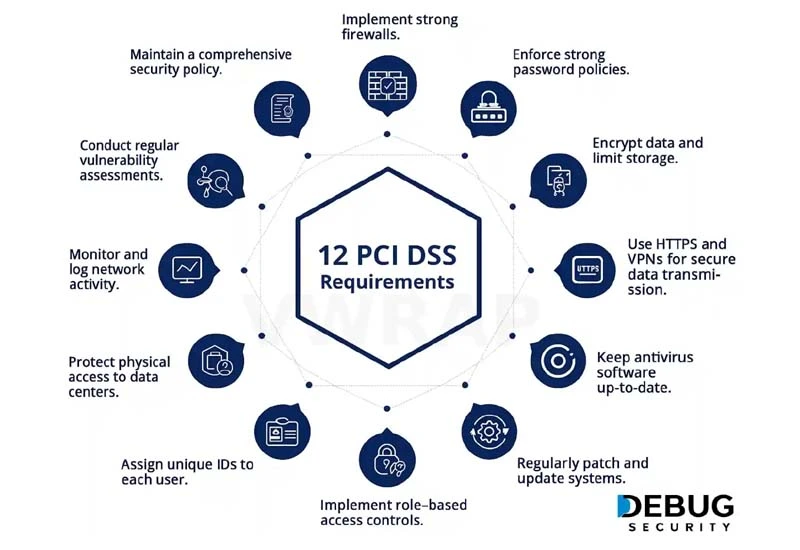
Standards and Guidelines
Debug Security provides professional penetration testing services based on internationally recognized cybersecurity frameworks. Our testing approach ensures high accuracy, risk coverage, and full compliance with both global standards and local regulations. We serve clients across various industries, meeting regulatory requirements in Bangladesh, including the Bangladesh Bank ICT Guideline, as well as European Union directives such as NIS2, the Hungarian Cybersecurity Act, and DORA. Debug Security helps organizations identify vulnerabilities, reduce cyber risks, and strengthen their overall security posture.
Penetration Testing Procedures We Followed
In our penetration testing methodology, we follow a structured, standards-based approach aligned with both international best practices and sector-specific regulatory requirements. The following frameworks and guidelines are integrated into our processes:
- Open Web Application Security Project (OWASP)
- MITRE ATT&CK Framework Guideline
- Application Security Verification Standard (ASVS)
- Open Source Security Testing Methodology Manual (OSSTMM)
- Open Source Intelligence (OSINT) Techniques
- Penetration Testing Execution Standard (PTES)
- PCI DSS Penetration Testing Guidance
Regional / Regulatory Guidelines
- Bangladesh Bank ICT Security Guideline (Applicable in Bangladesh)
Followed for financial sector clients in Bangladesh to ensure compliance with local regulatory expectations for ICT security. - EU and Hungary-Specific Cybersecurity Regulations (Applicable in Hungary)
For engagements in Hungary and the EU, we incorporate requirements from:
NIS2 Directive and the Hungarian Cybersecurity Act (Act LXIX of 2024)
Relevant for entities classified as “essential” or “important” under national law.
DORA (Digital Operational Resilience Act)
Specifically for financial sector clients regulated by the Hungarian National Bank (MNB) or EU financial supervisory authorities.
Advantages of Penetration Testing
Most organizations operate with a limited cybersecurity budget. Making the most of that budget requires strong protection across critical layers like applications, networks, and APIs.
Penetration Testing, or PenTest, delivers clear, data-driven insights into your current security posture. By simulating real-world attacks, Penetration Testing helps identify vulnerabilities before malicious actors do.
Why Choose Debug Security?
Debug Security follows proven, industry-standard methodologies to deliver accurate, detailed, and compliance-ready results. Each Penetration Testing is designed to provide complete coverage and align with security frameworks and regulations.
From web applications to complex infrastructure, every layer is thoroughly assessed to reduce risk and improve security posture.
The benefits of Penetration Testing are:
- Identify vulnerabilities in applications, networks, and APIs
- Ensure compliance with security regulations and standards
- Integrate easily with Agile and DevOps environments
- Gain actionable insights to fix security gaps quickly
- Improve customer trust with better data protection
Benefits of Working with Debug Security
- Certified cybersecurity professionals with deep technical expertise
- Custom-tailored assessments for businesses of all sizes
- Actionable reports with clear remediation guidance
- Alignment with industry regulations and compliance standards
- Commitment to client privacy, confidentiality, and long-term security