

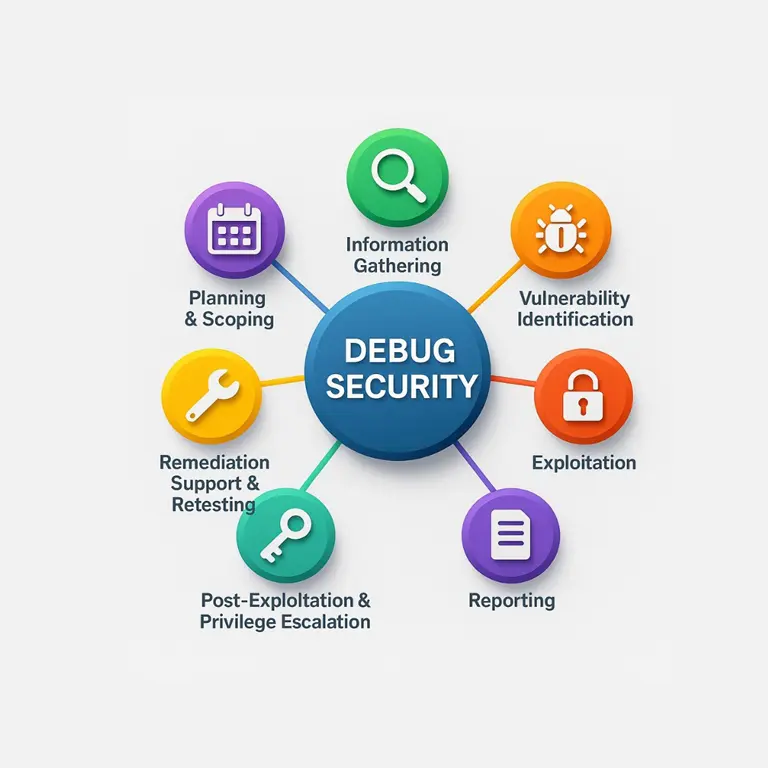
Define the scope and goals of the security engagement, including rules of engagement, target systems, and timelines. This ensures alignment between the security team and the client.
Collect data about the target system through passive and active reconnaissance techniques. This helps identify potential vulnerabilities and attack vectors.
Scan and analyze the target for weaknesses, such as outdated software, misconfigurations, or insecure code. This identifies areas that could be exploited.
Attempt to exploit identified vulnerabilities to gain unauthorized access or control over the system. This demonstrates how an attacker could breach security defenses.
Document the findings, including vulnerabilities, exploitation methods, risk assessments, and recommendations for remediation. This report provides actionable insights for improvement.
After gaining access, assess the extent of control an attacker could achieve by moving laterally or escalating privileges. This helps understand the full scope of potential damage.
Support the client in fixing identified vulnerabilities and verify through retesting that the issues have been successfully resolved, ensuring the environment is secure.